Last month, the OWASP Foundation announced the release of the 8th installment of the OWASP Top 10, as it typically does every few years. This release forces folks in AppSec, Product, and GRC roles to pause and assess whether they are training people on what causes breaches today.
As an Associate Director of Product Management, I’ve spent the better part of the last decade building application security training for enterprise learners, which encourages me to look at the 2025 update through a different lens. For me, this list isn’t just a “shift in categories” but a shift in how we build risk-aware teams, communicate risk to the business, and operationalize security training across diverse personas.
This post breaks down the changes and provides actionable guidance for CISOs, GRC leaders, AppSec managers, and training program owners.
A Quick Comparison: OWASP Top 10 2021 vs OWASP Top 10 2025
The 2025 list introduces two new categories, a major restructuring of supply chain risk, and the removal of SSRF as its own item:
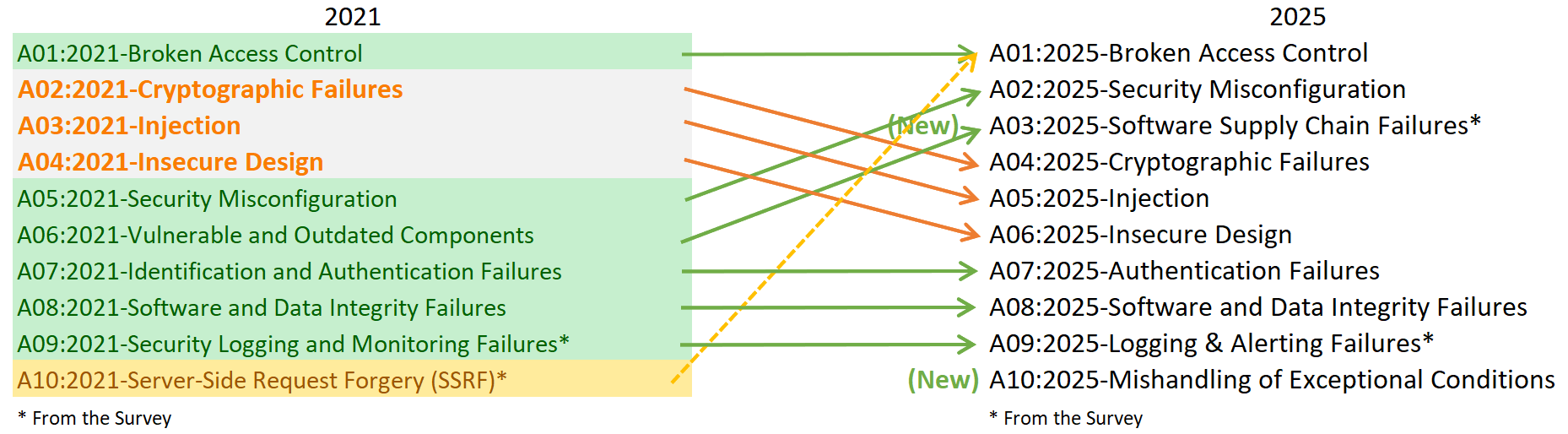
New or Elevated Themes
- Supply chain attacks are now mainstream, and OWASP formalizes them
- Cloud misconfigurations are now a top-tier concern
- Exceptional conditions get their own spotlight
- SSRF merges into Broken Access Control, reaffirming that authorization is the leading cause of breaches
New categories, such as A03:2025 Software Supply Chain Failures and A10:2025 Mishandling of Exceptional Conditions, signal that real-world attacks aren’t waiting for developers to write insecure code. Attackers are exploiting cracks in how code gets built, tested, configured, and deployed, stressing the importance of training all software stakeholders across the entire SDLC.
Why Business Leaders Should Care
Changes to the list don’t just have technical implications; they also influence:
- Audit readiness
- Customer assurance
- Vendor risk reviews
- Product quality metrics
- Team training strategies
- Investment in AppSec tools and processes
If you’re responsible for managing risk, not just the code, then this OWASP Top 10 update to impacts you.
How This Impacts Key Roles
CISO: This OWASP Top 10 provides CISOs with a clear narrative for identifying risk concentration areas to shape next year’s budget justification for training, tooling, and staffing, while misconfiguration issues directly map to modern breach root causes. This is the perfect time to conduct a training impact analysis to determine coverage gaps.
AppSec Manager/Security Engineer Lead: Update risk frameworks and assurance programs to incorporate the new categories into threat modeling, security requirements, and test plans. Enhance cross-team processes and tooling to enforce security configurations, supply chain hygiene, error handling, and logging/alerting. Make sure these priorities are integrated into CI/CD pipelines and security training.
Training / L&D Program Owner: Focus on updating curriculum. The OWASP 2025 affects course tagging, learning journeys, assessment questions, and the hands-on lab scenarios you deploy as part of your training program. Introduce microlearning pathways that tie each category to business impact.
GRC Lead: Understanding how these changes map to specific controls is important for updating policy language and risk register entries to reflect the 2025 terminology. The OWASP Top 10 intersects tightly with:
- NIST CSF Identify / Protect / Detect
- ISO 27001 A.5, A.12 / A.14
- SOC 2 CC series (CC3, CC6, CC7)
Breaking Down the Most Significant Changes
Security Misconfiguration moves to #2 – Configuration is one of the main factors that determines the attack surface. Cloud-first environments prove that the wrong toggle is as dangerous as the wrong line of code. Security training must teach secure config baselines, identity-bound permissions, secrets & environment variable hygiene, and IaC review techniques, which are all covered in the AWS and GCP courses released this quarter.
Supply Chain Failures become a category – Teams no longer treat packages, dependencies, and build tools as trustworthy by default. This is a maturity wakeup call that directly ties to vendor management and third-party risk. Training must now include how to evaluate package trust, dependency hygiene, SBOM literacy, and secure CI/CD operations.
Mishandling of Exceptional Conditions – This is a sleeper that finally gets the attention it deserves. Outages, timeouts, invalid states, and malformed messages often create the opportunity an attacker needs. Ensure your training includes safe logging practices, failing safely during unexpected conditions, and designing predictable system behavior under stress.
A Product-Led Roadmap for Adopting OWASP Top 10 2025
Phase 1: Awareness – Conduct a cross-team briefing and align on which OWASP categories map to critical business risks.
Phase 2: Training Refresh – Map your existing content to OWASP Top 10 2025, add new supply chain and exceptional condition modules, and introduce persona-based learning journeys for developers, DevOps, QA, and SRE.
Phase 3: Measurement – Track reduction in vulnerabilities tied to misconfigurations and authorization failures, build dashboards showing which teams are improving, and tie training outcomes to GRC reporting cycles.
Closing Thoughts
Regardless of your role, consider the OWASP Top 10 2025 as a conversation starter rather than a checklist. This long-awaited update presents an opportunity for stronger, more modern alignment among developers, security teams, and risk leaders. Whether you are accountable, responsible, or somewhere in between, this is the time to evolve your training strategy to meet the threats that exist today.
Base Camp has all the training content your organization needs to update your OWASP Top 10 program. Build a program that aligns to personas, risks, and GRC outcomes, not just vulnerability descriptions, to drive a culture of secure design.
Contact us today to learn more about our tailored learning journeys.