Picture the vast desert of open-source: shifting dunes of reusable packages, built and maintained by a global community. In this world, the original “sandworm” lurking beneath those dunes — Shai-Hulud — was already a nightmare; now, the worm has returned. The new mutant, Sha1-Hulud, is more aggressive, more stealthy, and more dangerous than before.
Sha1-Hulud: The Second Coming of a Worm
It's being called "the largest and most dangerous npm supply-chain compromise in history." According to researchers, between November 21–23, 2025, a wave of malicious packages appeared in the npm registry -- trojanized versions of otherwise legitimate packages used in major projects (including packages associated with Zapier, Postman, PostHog, and ENS Domains).
What makes this wave of malware particularly troubling:
-
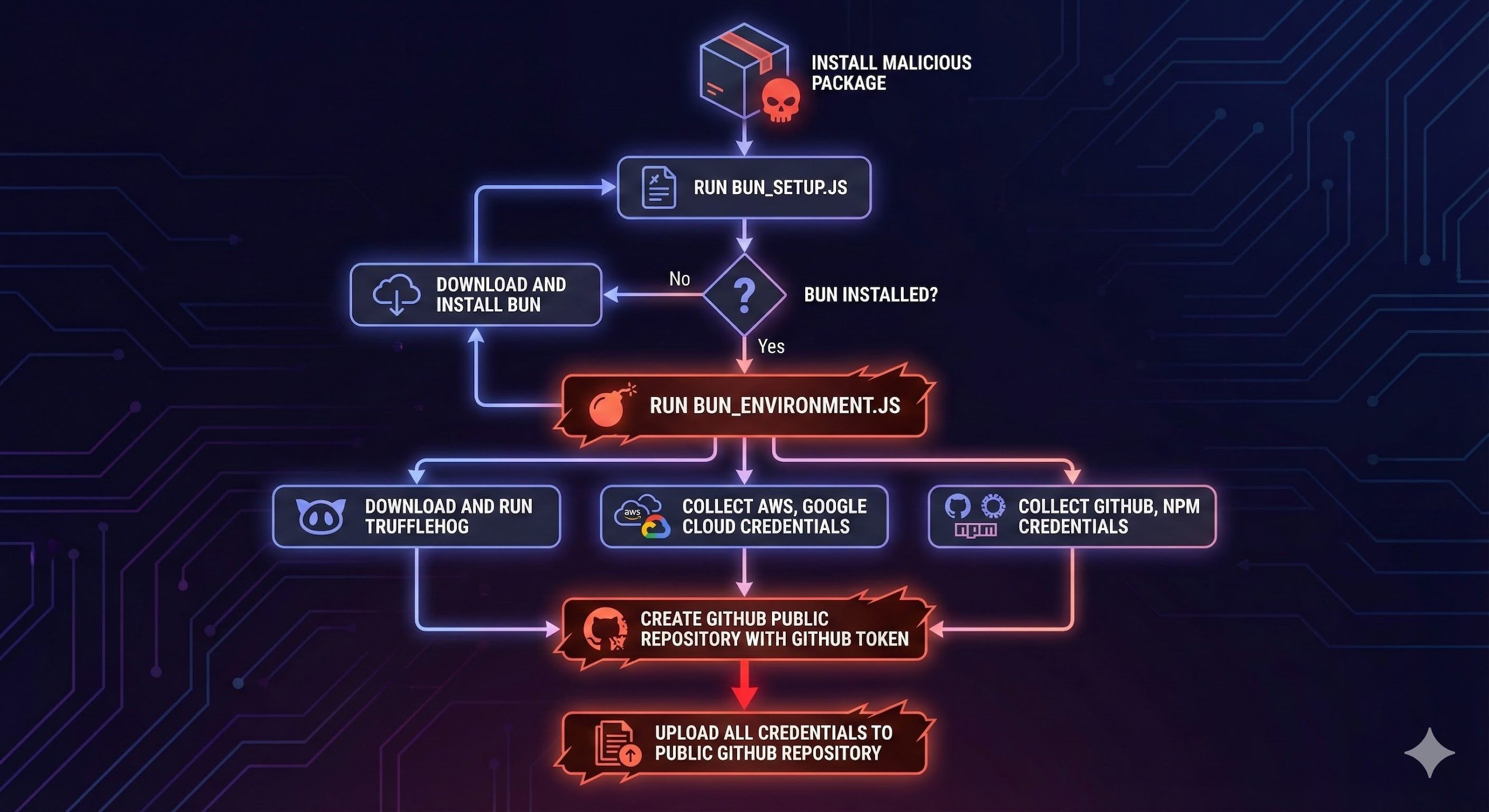
It executes during the pre-install (or install lifecycle) phase — a deadly shift from typical post-install trojans.
-
The payload is obfuscated and heavy (setup_bun.js, bun_environment.js), often designed to use a non-standard JavaScript runtime (like Bun), evading simple scanners and AI-based detection tools.
-
Once installed, the malware hunts for secrets: npm tokens, GitHub PATs, cloud credentials, CI/CD environment variables — then exfiltrates them via GitHub repositories or other hidden channels.
-
It doesn’t just stop there: with stolen credentials and automation tokens, it can republish infected packages, infecting up to 100 additional packages per compromised user, multiplying the impact exponentially.
In other words, once it lands, it spreads far and wide, devouring everything in its path.
Why Secure Code Training Matters
At first glance, this might seem like a technical issue that can be solved with better scanners, more rigorous CI/CD hygiene, or improved registry controls. But the root vulnerability is cultural. Developers are under pressure to move fast, and many treat third-party packages as trusted, reliable, and safe. That's the behavior that Sha1-Hulud is exploiting.
Through structured secure-code training and adopting best practices, teams can build muscle memory around several critical practices:
-
Dependency skepticism: Before importing any packages, especially recently updated packages, ask some basic questions: “Has this changed recently? Does the package execute scripts during installation? Do we really need it, or can we write a small in-house utility instead?”
-
Secrets hygiene: Never embed long-term tokens in code or in persistent env variables. Use short-lived credentials, ephemeral tokens, or secrets-vault solutions. Rotate keys regularly. Treat secret leaks as first-class risks.
-
Pipeline hardening: Disable or scrutinize package-install lifecycle scripts (preinstall, postinstall) in CI/CD. Use strict outbound-network restrictions for build environments. Require manual or automated vetting of dependencies before deployment.
-
Supply-chain visibility: Maintain a clear Software Bill of Materials (SBOM) for every project. Know exactly what’s in your stack — and who maintains it. If a dependency’s maintainer credentials are compromised, you don’t want to be caught unaware.
Adopting these practices broadly and promoting secure-code awareness as essential can keep malware like this from proliferating and mitigate far-reaching damage.
Shai-Halud May Be Fictional, but the Stakes Are Real
Fans of the Dune saga know that the original Shai-Hulud sandworm was an unpredictable and deadly force of nature, popping up without warning to wreak destruction. The worm was dangerous because the desert was unguarded.
Likewise, in today’s software deserts built on open-source dependencies, Sha1-Hulud thrives because many organizations are unprepared to defend against these exploits. By investing in secure code training, dependency hygiene, and supply-chain visibility, development teams can build protective “sietches”: safe strongholds in a hostile environment.
Bolstering Defenses with Proactive Education
Technical controls (scanners, removal of malicious packages, audit logs) are essential, but they’re reactive and imperfect. True resilience comes when your teams understand why supply-chain hygiene matters and build it into their everyday workflow.
CMD+CTRL offers learning paths tailor-made to address supply-chain risk, helping developers identify dependency risks, vet third-party packages, inspect obfuscated payloads, prevent malicious execution paths, and more. Just a few of our more than 250 courses deal with:
As we navigate this new wave of stealthy supply-chain assaults, the most cost-effective, scalable, long-term defense isn’t just code. It’s empowering developers, engineers, and security champions to adopt secure practices and establish repeatable and enforceable workflows.
If your organization isn't investing in secure code training, or if your developers still treat dependencies as black-boxes, you need to start now. When people are trained, and processes are designed to reinforce secure behaviors, your organization gains a resilient, proactive defense. The sands are constantly shifting, and the next desert worm may be more destructive.
Sources: